It appears some HP printers are provided with drivers which by default have the duplex functionality turned of at driver level, presumably because some other forms of the printer do not provide duplex functionality. Anyway in order to enable duplex functionality at driver level (which will allow programs such as Microsoft Word to perform duplex printing) just follow these steps:
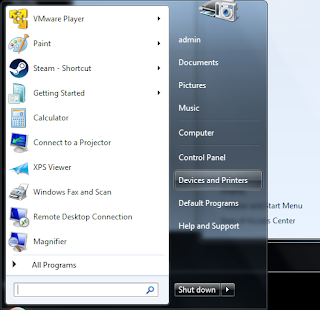
Firstly go to the "Printers and Devices" section from the Start Menu:
Now we will right-hand click on the target printer and select "Printer Properties":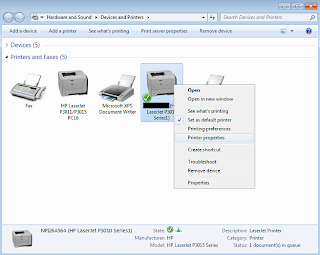
And finally we click on the "Device Settings" tab and change the "Duplex Printing" drop-down to "Installed". Apply the changes and then restart Microsoft Word etc.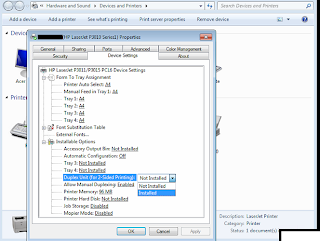
You will now have the ability to print duplex documents as below: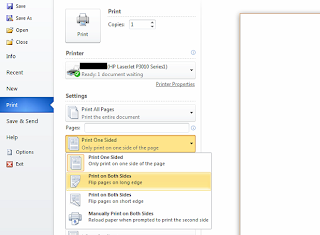

Now we will right-hand click on the target printer and select "Printer Properties":

And finally we click on the "Device Settings" tab and change the "Duplex Printing" drop-down to "Installed". Apply the changes and then restart Microsoft Word etc.

You will now have the ability to print duplex documents as below: